Risk Management
Policy/view
Reviewing the risks in response to the change of the social environment surrounding the company and appropriately responding to them are the preconditions for fulfilling the company’s social responsibility to its stakeholders as well as securing a sound business activity. Therefore, we manage risks that would inhibit the implementation of the “MAEDA Corporate Conduct Charter” based on the “MAEDA Risk Management Policy” and “Risk Management Rules.”
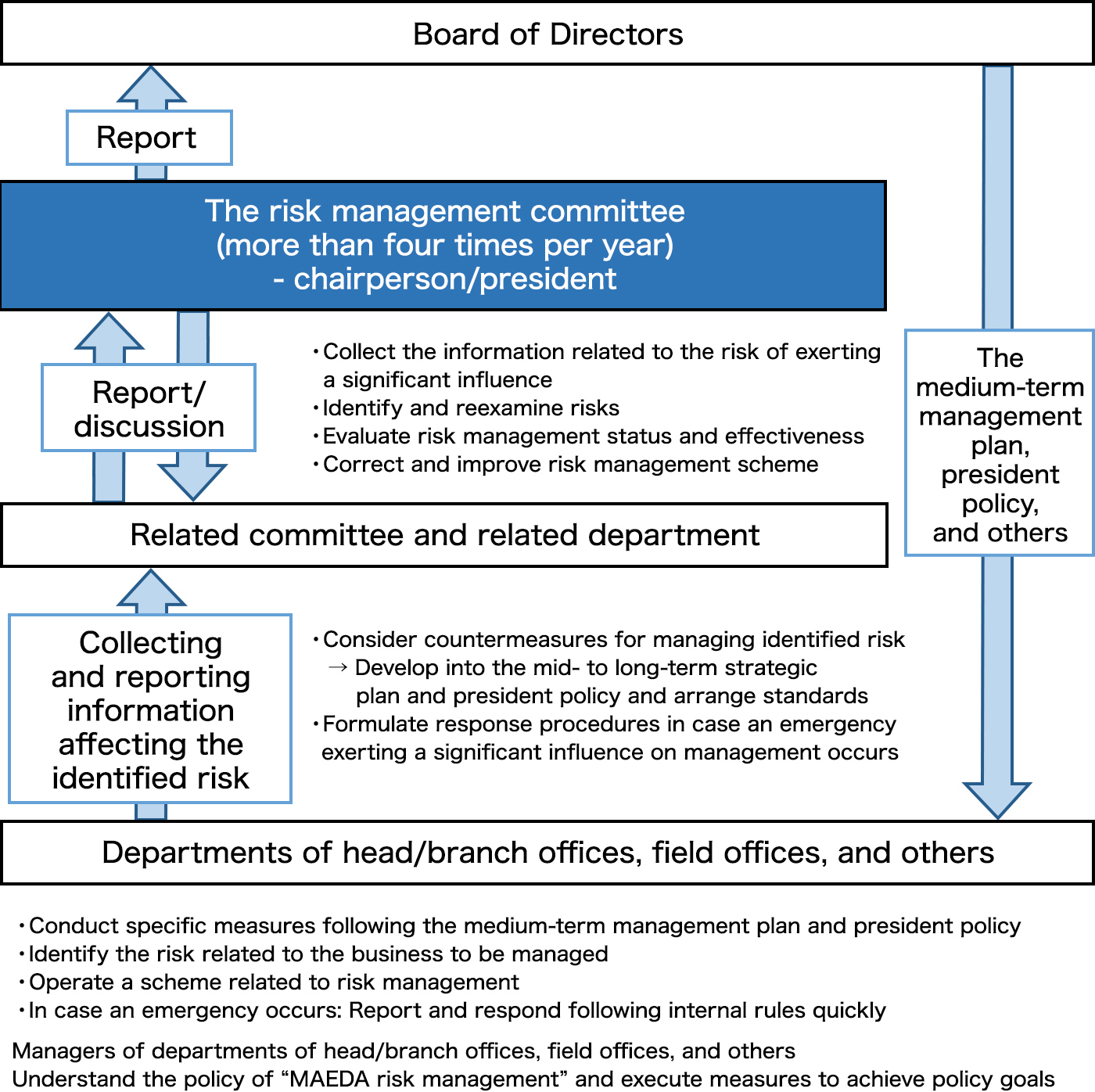
Risk management structure
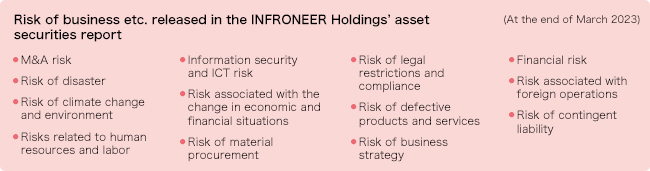
In addition, the results of assessment by the Risk Management Committee are reported to the Board of Directors every time the Committee’s assessment is conducted (every quarter) (see the following figure). We conduct business activities that take into account high-risk areas revealed in a “Risk map,” report risk-related information to INFRONEER Holdings, and disclose information on risks to the entire group through documents such as INFRONEER Holdings’ "asset securities report," etc., in a timely and appropriate manner. The business risk released in the INFRONEER Holdings’ asset securities report based on the information at the end of March 2022 is as follows. Also, the main examples of the response to risk information corresponding to the high-risk area in FY 2021 are presented in the following table.
Our Corporate Audit Department seeks to strengthen our internal control by conducting activities such as auditing based on risk assessment, and presenting a recommendation to the respective department for improvement. The FY 2022 audit was conducted at all departments of the head office, 10 branch offices in Japan, 20 field offices in Japan, and four group companies.
Also, the Safety, Quality & Environment Audit Department is conducting the “theme audit,” which is to be conducted by themselves, and the “MS audit,” in which management system (MS) auditors audit the MS, for safety, quality, and environment. In FY 2022, the theme audit was conducted at the head office (related departments), all branch offices in Japan, 19 field offices in Japan, and two group companies, while a MS audit was conducted at 158 field offices in Japan.

Response to risk information
in high-risk areas
| Item | Examples of major responses |
|---|---|
| Global environment (TCFD) |
|
| Corporate ethics |
|
| Information security |
|
![l Risk management committee: [KPI] Update of risk information at the risk management committee](/assets/images/english/csr/governance/rm/rm_img09.jpg)
![Report of updated information to the board of directors: [KPI] Report of update information to the board of directors](/assets/images/english/csr/governance/rm/rm_img10.jpg)
Internal Control
We recognize that to continually increase the corporate value of the entire group, it is essential for corporate management to utilize committees such as the intellectuals committee, as the advisory bodies for the board of directors, as well as to enhance our internal control function. We have conducted activities such as the improvement of our management structure with the aim of improving the management efficiency, integrity and transparency.
Internal Control Systems
To thoroughly implement internal control, we have clarified our basic policy for an internal control system, and improved the effectiveness of the internal control system by taking measures such as establishing a “CSR Strategy Council” and “Risk Management Committee,” which are chaired by the President and consist of management personnel, and a “Corporate Audit Department,” which conducts audits independently from the executive department.
Internal reporting system
To respond to the Whistleblower Protection Act amended in June 2022, we newly established the internal reporting rules and the Legal & Compliance Department has taken charge of the operation of two report reception windows.
One of the windows is the “Hotline for the workplace.” This is an external window entrusted to Cuore C Cube Co., Ltd. Not only the executives and regular employees of our company, but also those of group companies can use it on the intranet. They can report harassment and compliance issues and also consult about working relationships.
The other is the “Compliance hotline.” This window is placed on the external website of our company and external users such as customers can also use it.
The total number of reports received at both the windows in the first half (of the 78th fiscal year) was 76. To discover internal improper conduct and promote compliance management as soon as possible, the Legal & Compliance Department is trying to disseminate the internal reporting system through internal bulletin boards and seminars and promote its use.
Exclusion of anti-social forces
As part of our internal control, our company has established a system for disconnection of any relationship with anti-social forces. We have stipulated this issue also in our Corporate Conduct Charter, seeking to educate our employees and familiarize them with the issue in employee training programs.
BCP
Our company's basic policies for business continuity are to understand the damage situation of the site that is under construction and the site that has been delivered after first ensuring the lives and safety of employees and their families and respond to social demands, such as infrastructure restoration and rescue requests from surrounding areas. In addition, our company has formulated a “Business Continuity Plan,” and the plan has been certified by the Kanto Regional Development Bureau, Ministry of Land, Infrastructure, Transport and Tourism. In preparation for disasters, we conduct BCP drills once a year in principle.
Last year we conducted the training in November for the purpose of enhancing the wide-area cooperation between the head office and branches on the basis of the damage estimation on the Nankai Trough Megathrust Earthquake published by the Cabinet Office.
The training was practical with the use of ICT, including the trial of a new system and check of damage situations by a drone in the event of a disaster, so that the range of response measures was expanded.
We will enhance the reporting and communication system with the conduct of reporting to the holding company, confirming the safety of the cooperating companies, etc., deepen the cooperation between the cooperating companies and the group companies, and continue to make efforts while turning our attention to regional collaboration and support in disaster prevention.

![Effort for BCP: [KPI] answering safety confirmation emails in BCP drills (within three hours)](/assets/images/english/csr/governance/rm/rm_img06.jpg)
An information security structure and efforts
As IT technology advances, cyberattacks have also become sophisticated and complex. Under the Cybersecurity Management Guidelines (by the Ministry of Economy, Trade and Industry), management executives are strongly required to be involved in corporate information security. Thus, information security is an important issue for management.
Our company strives to establish an information security management structure and prevent defects in accordance with the “MAEDA Information Security Policy.”
We have worked hard on strategic and efficient productivity improvement using IT since fiscal 2017, and at the same time, in order to respond to such a crisis, we have further strengthened the information security structure for the entire company, and have promoted the following activities.
- (i) A unified management structure achieved by the “Supervisory Manager for Company-wide Information Security”
- For the information safety system for the entire company, we are adopting a unified management structure achieved by the “Supervisory Manager for Company-wide Information Security” appointed by the president. Also, “the Supervisory Manager for Company-wide Information Security” appoints the “person responsible for information security, who is in a higher-level position than a group manager, understands the business of each department and field office, and has authority and responsibility for information security.
- (ii) Formulation of an “information security activity plan” for the entire company (all departments)
- To prevent a major accident related to information security from occurring, under the entire company information security general manager's instruction, the information system general center drafts the "information security activity plan." Based on the entire company plan, all departments of the head office and branches create and implement the "information security activity plan."
- (iii) Establishment and operation of information importance categories
- We have specified information importance categories common across the company, and established a method of operating them. In the process of those activities, we have defined the most important information (category A information) as “information that would substantially affect our company’s performance and would cause significant problems with operation, if it was lost,” and have established a mechanism for preventing its leakage. Specifically, we have attached an IC tag to most important paper-media information and have stored it in a locked locker. As for the information saved in electronic media, files have been encrypted and stored in an access-restricted folder.
We continue to maintain no cases of leakage of the most important information, and no cases of risk revealed. - (iv) Conduct of e-learning for information security education
- We are carrying out information security education e-learning for all employees to improve their information security consciousness. Furthermore, all employees who have completed the e-learning course have submitted a pledge on information security to the President. In addition, we are providing the targeted attack email training for all employees and temporary employees.
- (v) Implementation of external security diagnosis
- We find potential vulnerabilities of the information system in advance, take measures, and implement the external security diagnosis to minimize security incidents (risk).
As a part of the improvement in information security, the departments involved in the next customer's confidential information and the departments engaged in information control acquire the certification of the international standard of the Information Security Management System (ISMS) JIS Q 27001: 2014 (ISO/IEC 27001: 2013).

Technical development, technical assistance and fiduciary obligation in the ICI General Center
・Business at Information System Center
ISMS basic policy and registration information
Considering the cases of information leakage and personal information outflow in recent years, our company promotes information security measures related to internal organization improvement, management of information assets and human resources, entering and leaving management, hard and soft protection, etc.